April 12, 2009
Operational losses, much more than a tail only!

- Image via Wikipedia
Introduction.
This article is about operational losses and how insight in these losses can be extremely valuable for any organization. It describes a best practice approach for the implementation of loss recording and reporting. It will not dive into the modelling of operational risk, because for that subject there is plenty of information available. For those less familiar with operational risk management, an operational loss represents (potential) financial or reputation damage as a result from a failing human, system, process or from external threats. Some examples for a bank:
bank robbery
delayed or not executed transactions
advice inconsistent with customers risk profile
documentation lost, incomplete contract
fraud
Background.
Most financial institutions collect operational loss data to model extreme operational risk events. These events are usually found in the tails as calculated by means of Monte Carlo simulations. The effort of collecting data and model operational risk is often driven by the goal to become Basel II compliant. The more advanced the operational risk program of a company is, the less regulatory capital needs to be set aside as a buffer against extreme events. The operational risk management requirements to become Basel II compliant are set by the BIS and require approval from the regulator. The objective of the Basel II accord is to stimulate development of advanced risk management methods. Banks have the economical need to keep the regulatory capital as low as possible and at the same time need to prove to investors and rating agencies they have robust risk management practices in place.
Although the focus on the extreme event or the reduction of capital is understandable, the side effect is also that an organization often forgets to fully leverage the power of insight in losses. This insight really can boost risk awareness and the self learning capacity of an organization and at the same time dramatically reduce costs resulting from failures.
Loss management for business as usual.
Who needs to record losses?
When setting up loss registration you first have to consider what type of organization you need to facilitate. There is a difference between an organization that offers low frequency, high value and tailor made financial products or an organization that offers high frequency, low value standardized and highly automated services.
In the first case you can assign the responsibility to register the losses to the ORM unit simply because the frequency is low and most losses will have a considerable impact and will require detailed and immediate analysis. In the latter the number of losses can be considerable and probably recurring. In this situation it is best to make the operational business units responsible for the registration of losses in the loss database. When you have to build up your loss management from ground up, there is one important other consideration. A big part of the information you need probably is already in your complaints management system. Consider extending your complaints management system with an interface to your operational risk management system to avoid manual duplication of readily available information.
Now there are different approaches in use to distinguish losses from other financial transactions. Some banks use the centralized approach to detect losses by validating general ledger entries to see if some need to be flagged as operational losses. I think this method has only one major advantage and many drawbacks. It usually requires limited effort to implement this, but has the drawback that it is very likely that many operational losses will remain undetected and information is incomplete. In other words, the advancement of insight in your organizations operational risk will remain limited.
The decentralized detection and recording approach demands much more effort from the ORM unit. It requires that almost every departments needs to understand what operational losses are and how to record them. However once it is in place you’re in business. The simple fact that the business is recognizing and recording operational losses is the best starting point to improve and sustain risk awareness and management at operational level. By ensuring you can aggregate these losses you will be able to present an operational risk heat map for your organization and manage operational risk at tactical (product) and strategic (company) levels. It is advised to combine the recording of losses with the financial booking of the loss. This way you add an additional quality and integrity layer to your loss recording process simply because financial accounting controls are put in place. It will help you to avoid discussions about the correctness of the loss data and also who is responsible for this correctness.
Now what about legal claims or potential regulator fines? These need to be recorded in your loss management system before a financial transaction, if any, will occur. Once it is clear if there will be any financial impact simply follow the regular procedure and make sure no double recordings can happen.
In all cases it should always remain the responsibility of the business, not the ORM unit, to record all losses timely, completely and correctly. Below you find a high level loss management process flow. I would like to put some emphasis on the third step. The assignment of the loss should be tied to acceptance by the loss bearing unit of the loss. This confirmation that the responsibility for the loss is accepted adds to the quality of information as well as to a sustained risk awareness at operational levels in your organization.
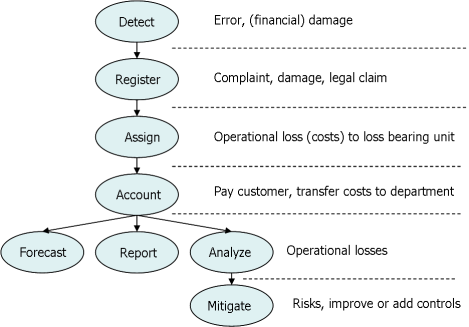
Who needs to pay the loss?
Losses should be accounted for per business line as prescribed by the BIS. The losses are input for capital calculations and subsequently capital is assigned to profit centres. However, you also want to make visible who is responsible for the losses that occur. In general it is best to assign the losses to the department that is causing them. Now the occurrence of some operational losses are acceptable as part of the design of a product or process. For instance losses that result from skimming a debit card carrying information on a magnetic stripe. These losses should be assigned to the product owner. Other losses result from wrongful execution of procedures. These losses should be assigned to the department that caused the non-adherence to the procedure. Sometimes losses are caused by service providers. It’s is best to assign these losses to the department who owns the contract with that service provider.
No matter what, when customers have to be paid it speaks for itself that the loss management process should never delay the payment.
What needs to be recorded?
All operational losses above a certain threshold need to be recorded. Although one can decide to minimize the administrative effort by increasing the threshold, it is better to start with a low threshold and optimize the threshold after a few years of experience. Working for a retail organization it is my experience that a threshold of 1000 Euro works well and I think this is a sensible threshold for any organization. The idea behind this is that most errors with a relatively low financial impact can also result in incidents with a high financial impact.
For modelling and benchmarking purposes an organization can become member from ORX or ORIC. These organizations work with thresholds of 20.000 dollar and £ 10.000 , so the threshold of 1000 Euro, pound of dollar will fit. When setting a loss threshold the thresholds from ORX or ORIC should not be considered as a guideline for an organization because the purpose is totally different as I will show later.
Now what attributes does a loss record have? You should take the minimal requirements from BIS and ORX or ORIC. I’ve outlined these requirements here, but I do not promise that they remain up to date.. Just check with ORX or ORIC.
• Reference ID number (Member generated)
• Business Line (Level 2) Code
• Event Category (Level 2) Code
• Country (ISO Code)
• Date of Occurrence
• Date of Discovery
• Date of Recognition
• Credit-related
• Gross Loss Amount
• Direct Recovery
• Indirect Recovery
• Related event Ref ID
This list is an excellent example to demonstrate why loss management has different purposes. When loss management is limited to these attributes it can only be used for benchmarking. When you want to use the information for internal analysis to reduce losses or review controls there is a variety of attributes missing. For internal analysis and reporting you also need to record:
Type of loss i.e. operational loss, operational loss component of a credit loss, (legal) claim.
A descriptive text outlining what has happened and why.
Which department needs to take this loss in its books.
Which department did cause this loss (more explanation later on).
Loss event category i.e. what event occurred (very easy to make fundamental mistakes here).
Loss cause category i.e. what caused the event that resulted in the loss.
Product or service like mortgages, credit card, loan etc.(usually requires more hierarchies).
Now this all sounds pretty straightforward, but there are generic issues that probably require some additional effort to ensure alignment with other supporting processes. It is recommended to align your product and services list with financial reporting and complaints management. This will allow you to incorporate more easily operational losses in your cost reporting and correlate operational losses with customer complaints. Furthermore you are advised to ensure for reporting purposes you will be able to aggregate losses at each hierarchical level in your organization and aggregate at product and product group level.
When you intend to apply for Basel II compliance it is mandatory to use standard loss categories. Unfortunately when you limit the loss recording to those categories your loss analysis and reporting capabilities will be severely impacted. The problem with these categories is that they are often to vague and when used in aggregated loss reporting do not allow a manager to set priority or take action. A potential solution is to connect these mandatory categories to your business defined categories, but not show them in the loss management process.
When do losses need to be recorded?
Losses should be recorded (and booked) within a short period after detection. The larger the loss the more difficult this will be, but a limit of 20 days should be do-able. For large (potential) losses you can decide to design a same-day emergency reporting process to inform senior management more quickly.
For operational losses that are part of a credit loss there is a difficulty. Most of these credit loss components, with the exception of fraud, usually emerge at the moment when a loan defaults. The best approach is to record at the earliest possible time i.e. just after detection.
Where do losses need to be recorded?
Preferably losses are recorded in a central loss database and off course in the general ledger. This way it is easy to report and to get central oversight of operational losses trends. Centralized storage is also beneficial for operational risk modelling, forecasting and Basel II compliance. It also allows you to analyze losses and determine where the concentrations of losses can be found.
What quality controls could be implemented?
One important control is a frequent sign off by management stating the full coverage, completeness and correctness of recorded losses. A review of the ORM department from the correct recording also should be considered, preferably combined with the analysis of the important losses. Ensuring the quality is important for modeling, reporting and analysis. Combining this review with the reconciliation of the loss database against the general ledger also adds to the quality and the trustworthiness of the information.
What to do with the loss information?
The added value of the operational loss information is already outlined in various places in this overview. One of the most important things you should do with losses is ensuring frequent (monthly) reporting at all levels of your organization. This way you enable management to develop risk awareness and manage actively operational risks or failing controls. You could also use loss information to create a set of Key Risk Indicators (KRI) or as input for a risk heat map.
Usually loss recording is required to model operational risk as part of a Basel II compliance application package. Using losses to measure the quality of execution in your organization by incorporating loss thresholds in performance contracts is taking it one step further. Losses are backward looking, but by analyzing losses in detail you can also develop operational risk indicators. Indicators that signal an increased level of risk which require management attention to avoid increase of losses. Loss information can also be used to review your insurance strategy.
I’ve outlined many examples to take advantage of operational loss information in a business as usual environment. But the best example is given by this citation of a senior manager from a large bank. Immediately after assuming a new position he asked for two things: “Show me the losses and show me the audit findings so I can see whether or not we are in control”.
Summarizing Key success factors for operational loss management.
- implement loss detection and registration process at the lowest level in your organization
- combine this process with the financial accounting of the operational loss
- provide clear guidance on how to allocate the loss
- make sure event categories are aligned with the business processes
- report monthly at operational, product and hierarchical levels. Report concentrations, trends and forecasts.
- incorporate loss frequency in the performance contracts
Summarizing key benefits of operational loss management.
- reduced regulatory capital
- reduction of costs
- sustained risk awareness at all levels in your organization
- transformation of incident driven management into risk/reward management
- improved insight in performance of recovery departments (legal, security, etc)
Conclusions.
This article outlined the added value of an operational loss management process in a business as usual context. The process will improve the learning capability of an organization. It also can be a very effective instrument to reduce costs. This practice has been developed for financial institutions, but should be considered for any medium to large organization.
A careful implementation of the process is required to leverage the potential to the full. It will require backing from senior management with the ambition to improve transparency. Following mandatory guidelines from BIS and regulators is as important as alignment with day-to-day business processes.
January 13, 2009
News from GTNEWS
Today I’ve added the RSS feed from gtnews to my collection of high quality risk related feeds. Although not all articles are risk related, the depth and the quality of their articles deserve the opportunity to show up in the daily news stream. Njoy!
September 29, 2008
Credit crisis bankparade interactive.
Now credit crisis events are spreading to Europe an update of the extensive credit crisis overview was necessary. Follow this link to the guided analysis for an interactive experience or follow this link for a graphical view on the crisis. Investors assume that all problems are credit crisis related. The Fortis problems are however the result of a bad timed take-over of ABNAMRO, bad communication of capital ratio recovery actions and lack of trust in the capability of Fortis to obtain the required investments in time. From an operational perspective the bank claims it is a healthy business still generating revenues. The issues in England are different from those in Belgium and the Netherlands. The housing market in England is also deteriorating and combined with the lack of confidence in banks this has resulted in the take-over of several mortgage lenders. However, prudent banking is still there. Another company that participated in the ABNAMRO take-over has enough cash to roam the financial world for interesting bargains. Santander already showed after the take-over of ABNAMRO it is able to act swiftly, decisively and with success. As part of the take-over it acquired the Brazilian bank Banco Real and the Italian bank Antoveneta. It quickly sold Antoveneta to another Italian bank and now has the power to profit from the opportunities the credit crisis offers. Today it was announced Santander only had to pay 600 million euro for 21 billion euro in deposits and acquired also the branches of Bradford and Bingley. Earlier this year it obtained the European banking assets from General Electric. It shows the big differences between banks that joined the team that bought ABNAMRO one year ago.
September 16, 2008
Merrill take-over by BofA, an informed decision?
Yesterday I expressed my concerns regarding the rational behind the take-over of Merrill Lynch. Today several commentators are wondering why BofA is willing to pay much more than the market value. It seems obvious there is more to it than the public at this moment knows. What is in it for BofA? Maybe there is a reason to share this with BofA’s shareholders? The initial view of analysts is that it probably is a forced deal and I’m inclined to agree with this. One day after the “deal” the is a general concern whether or not BofA can absorb Merrill’s troubles. It is almost impossible to make an informed decision on such a short notice. What guarantees have been given to BofA to take this risky jump in the dark? Another interesting question is whether or not it is possible to manage two take-overs in a period that is causing serious problems for every company in the financial industry.
From a BofA perspective a Lehman take-over would have been much more transparent. Although the risk management of Lehman proved to be inadequate, the management of Lehman in general has a much better track record when you look at business ethics or management integrity.
In the past year Merrill has been accused of many things except high moral standards. I’m really curious how many billion dollar surprises will emerge once BofA really takes over control. Revisiting the credit crisis events show that a reduced level of management integrity proved to be a reliable key risk indicator of corporate failure in difficult economic times. To substantiate this I’ve included a list of Merrill events covering the last 12 months. This list was extracted from the Riskfriends guided analysis. BofA shareholder read and think again!
|
Date |
Event |
Detail |
|
2008-09-14 |
Take over |
Bank of America did take over Merrill although it was |
|
2008-08-21 |
Law suits |
Agreed to buy back $ 12 billion of ARS and pay a fine of $ |
|
2008-08-04 |
Integrity concerns |
Merrill suspected of colluding with UBS manipulating the |
|
2008-07-29 |
Capital ratio recovery |
Planning to raise another $ 8.5 billion |
|
2008-07-29 |
Investment lost |
Lone Star Funds buys CDO’s from |
|
2008-07-23 |
Law suits |
Los Angeles |
|
2008-07-18 |
Capital ratio recovery |
Sold Bloomberg part back to the company for $ 4.4 billion. |
|
2008-07-18 |
Write off |
Totaling $ 9.4 billion, 30 percent CDO, 30 percent credit |
|
2008-07-07 |
Capital ratio recovery |
Selling parts of Bloomberg and Blackrock to raise another $17 |
|
2008-06-26 |
Prediction |
$ 4.2 billion write off predicted for the second quarter |
|
2008-04-18 |
Law suits |
Pension fund CtW investment |
|
2008-04-18 |
Job cuts |
2900 jobs in reaction to write down |
|
2008-04-17 |
Write off |
$9.5 bllion |
|
2008-04-02 |
Capital ratio recovery |
$12.2 billion raised so far |
|
2008-03-18 |
Liquidity issues |
Wachovia states that the exposure of Merrill is 3.3 the |
|
2008-03-11 |
Integrity concerns |
Congress questions Stanley O’neal |
|
2008-03-06 |
Job cuts |
Merrill Lynch said that it would stop making subprime |
|
2008-02-27 |
Investment lost |
Auction rate securities from Merrill |
|
2008-02-26 |
Management leaves |
CEO O’Neal steps down |
|
2008-02-08 |
Investigation |
SEC received request for information from the federal |
|
2008-02-07 |
Integrity concerns |
Accused by Massachusetts of fraud |
|
2008-02-01 |
Investment lost |
Merrill buying back $ 14 million of CDO’s |
|
2008-01-16 |
Write off |
$ 9.8 billion loss, write down $14.1 |
|
2008-01-15 |
Capital ratio recovery |
$ 6.6 billion cash raised issueing |
|
2008-01-14 |
Integrity concerns |
Finra investigating possible |
|
2008-01-11 |
Portfolio deterioration |
$15 billion write down expected |
|
2008-01-04 |
Integrity concerns |
Accused from hiding losses while merger was pending |
|
2007-12-24 |
Capital ratio recovery |
$ 7.5 billion acquired selling shares 13% below market |
|
2007-11-08 |
Integrity concerns |
SEC starts investigation investments |
|
2007-11-07 |
Portfolio deterioration |
Expected write offs 4th quarter another $9.4 according to CreditSights |
|
2007-11-03 |
Integrity concerns |
Merril not aware of |
|
2007-10-31 |
Law suits |
Lawsuits by shareholders |
September 7, 2008
Fannie Mae and Freddie Mac history!
This sunday will become in retrospect a remarkable financial date. The American government takes over control of two financial companies and replaces their CEO’s. The intention is to calm down the US financial market. The intervention signals great concerns and I wonder how the markets will react. The investors that once thought they were investing in shares with a low risk profile by now have learned a very expensive lesson. Fannie and Freddie lost over $ 120 billion in share value since October 2007.
When you want to view the Fannie and Freddie events that led to this historical event, just look here for Fannie and here for Freddie . Follow the OLDER link when you want travel back in time. You can initiate directed searches yourself, for instance by typing in “paulson freddie” without the quotes in the search box.
This event was also a signal to update the guided analysis. This covers by now over 500 credit crisis events! You can use this facility to analyze the credit crisis categorized events yourself.
August 28, 2008
Reporting Key Risk indicators, what to select?
Introduction
In the previous article with regard to the reporting of key risk indicators, the importance of a structured approach towards selection of KRI’s was explained. It also explained why an solid information infrastructure is a prerequisite of a reliable KRI environment. In the midst of the credit crisis it is almost a certainty that regulators in the near future will demand high quality risk reporting environments within financial institutions. An reporting environment that is complete, accurate and close to day-to-day business operations. The underlying KRI production process should be just as transparent as the produced KRI’s. Ratings agencies as well as regulators are expected to demand insight in how the reporting process is controlled just as they require external validation of the risk models in use.
Approach.
In many organizations a modern information infrastructure for KRI reporting will be missing. This doesn’t mean KRI’s cannot be reported. It does mean however that it will cost a lot of effort. It also limits the reporting to Key Risk effects only. Reporting more forward looking metrics like risk causes and control effectiveness as well as putting Key Risk effects into the right business context are simply not do-able when reports are build manually.
The following questions need to be answered before setting up KRI reporting:
- To whom will the KRI’s be reported, the board, product owners or operational managers?
- What are the main objectives at each management level and how specific are these objectives?
- an owner
- an end date
- objective
- upper and lower thresholds
- near real-time measurement
- Strategic
- Financial
- Market share
- Human capital
- Shareholder value
- Sustainability
- Control efficiency
- Tactical
- Financial
- Commercial
- Operational excellence
- Control efficiency
- Operational
- Costs
- Excellence
- Percentage hands free processing
- Control efficiency
- What Key Risk effect information is readily available that can signal impact on objectives and are the metrics and thresholds aligned with each other?
- General provisions
- Operational losses
- Complaints and legal claims
- Regulator fines
- Employee training budget
- Staff turnover
- Accepted risks
- Information quality
- Known high risks
- Software patch backlog
- Change management frequency
- Expected loss frequency impact on operational excellence.
- Expected loss amount impact on RAROC or Economic Capital.
- Expected loss amount impact on efficiency ratio.
- Expected complaint frequency impact on customer attrition.
- Expected number of risks without mitigation impact on control objectives.
- Expected internal fraud frequency impact on control objectives
- Expected change frequency impact on service availability
- Is it possible to transfer the presented Key Risk effect information into owned actions?
- Is it possible to measure the quality of the Key Risk effect information and is the owner willing to provide the requested information for this purpose?
- Try to construct groups of KRI’s which improve the interpretation of presented metrics. For instance construct a KRI group of complaints, claims and losses. These KRI’s are related and trending of the individual KRI’s in most cases should correlate.
- Extract information directly from your core systems. Think of information from systems like the General Ledger, marketing information, product specific operational data, human resource administration etc. The KRI system should not use manually corrected information. When information extracted from core systems is not reliable this is an issue that should be solved and not circumvented. It can help to get these issues on the priority list to make this visible in the KRI reporting.
- Demand that the presented information is not older than one day. This way business can respond quickly to changes in the risk profile and is also able to see quickly whether or not initiated actions have the desired effect. It forces the organization also to implement a fully automated and transparent KRI reporting solution. This reduces the risk of human error or manipulation of information and in the long term also is more cost efficient.
- Request from the information owner a statement of completeness and correctness to get insight in the quality of information. Many KRI’s use information from business supporting processes like financial accounting, complaints and claims, audit, credit and operational loss registration, human resource administration etc. This is information not validated by customers and the quality cannot not always be guaranteed.
- Ensure there is an information delivery contract which makes the information owner responsible for the timely notification of changes in the core systems. This way adjustments in the reporting environment can be planned.
Each management reporting level does have it’s own characteristics. The first difference is the level of aggregation. The board probably only wants a specification of KRI’s aggregated at organization level “board minus one”. Sometimes also a risk type view (like country or compliance risk) or a product view is also desired. To make the information interesting, the Key Risk Effects preferably are expressed as forecasts of relative impact on personal objectives. This way the KRI report is positioned as a tool to manage personal performance contracts too.
Different management responsibilities result in different objectives, although it is a best practice to align strategic, tactical and operational objectives. The level of reporting also impacts the characteristics of the reported KRI’s. At strategic level a KRI should reflect the outcome of different scenario’s. At operational level a YTD metric combined with a year end forecast is probably more than sufficient. Finding specific objectives with owners is not that simple. Some of the required attributes could be missing. An objective should have at least
Referring to performance management and balanced score card approaches you find some type of objectives categorized at the different decision levels:
Find readily available Key Risk effect information that signal impact on one of more of the aforementioned objectives. This information is usually already available in a different context. Some example Key Risk effects are:
Bottom line is that metrics are used that signal a potential direct negative impact on objectives. Some of these KRI’s appear to be backward looking, but can be made forward looking using regression techniques. Ideally there is enough history information available that can be used to reliably forecast end-of-year results. The next thing that needs to be checked is if these metrics are normalized. In other words, does the information from one source match with that of another source. For example: the recording of complaints doesn’t necessarily use the same product categories as for instance the financial accounting or sales force system. Relating KRI’s to objectives is not that difficult provided some alignment is inplace. Some examples:
For reported KRI’s it is a requirement that these KRI’s have business owners. It should be clear who is responsible for managing the KRI. KRI’s at different dimensions (organization, product, distribution channel, customer segment) can have different owners. When building a KRI reporting environment it helps to have a clear understanding how these different dimensions relate to each other. When an organization has a mature performance management environment, this should not be that difficult. In the situation this is lacking this impacts the effort needed to construct the KRI solution. Another thing that requires planning is the functionality needed after the reporting is in place. When KRI’s signal that objectives are at risk, management will demand action to address the risk. This requires people with analytical skills, high quality information and the tools to execute the analysis. In many cases it doesn’t make sense to report KRI’s when it is not possible to analyze the underlying information.
One of the first things management usually wants to know is how reliable the KRI information is. To make sure management doesn’t draw the wrong conclusions the KRI solution needs to be extended. The following quality measures should be considered:
Conclusion.
Creating a professional KRI reporting environment is a demanding task. The main success criteria to succeed are:
- Alignment with performance management preferably at the individual level. This way the KRI-reporting can be positioned as a tool that supports management with managing their objectives (and bonus).
- Top down approach with adequate and persistent backing from senior management.
- The creation of an information value chain that extracts and processes fully automated information from multiple core systems.
- Creative professional analysts familiar with predictive modeling and with access to the information and tooling to analyze and model.
- Consistent and transparent risk and performance reporting at strategic, tactical and operational level to align management of priorities.
![Reblog this post [with Zemanta]](https://i0.wp.com/img.zemanta.com/reblog_e.png)











You must be logged in to post a comment.